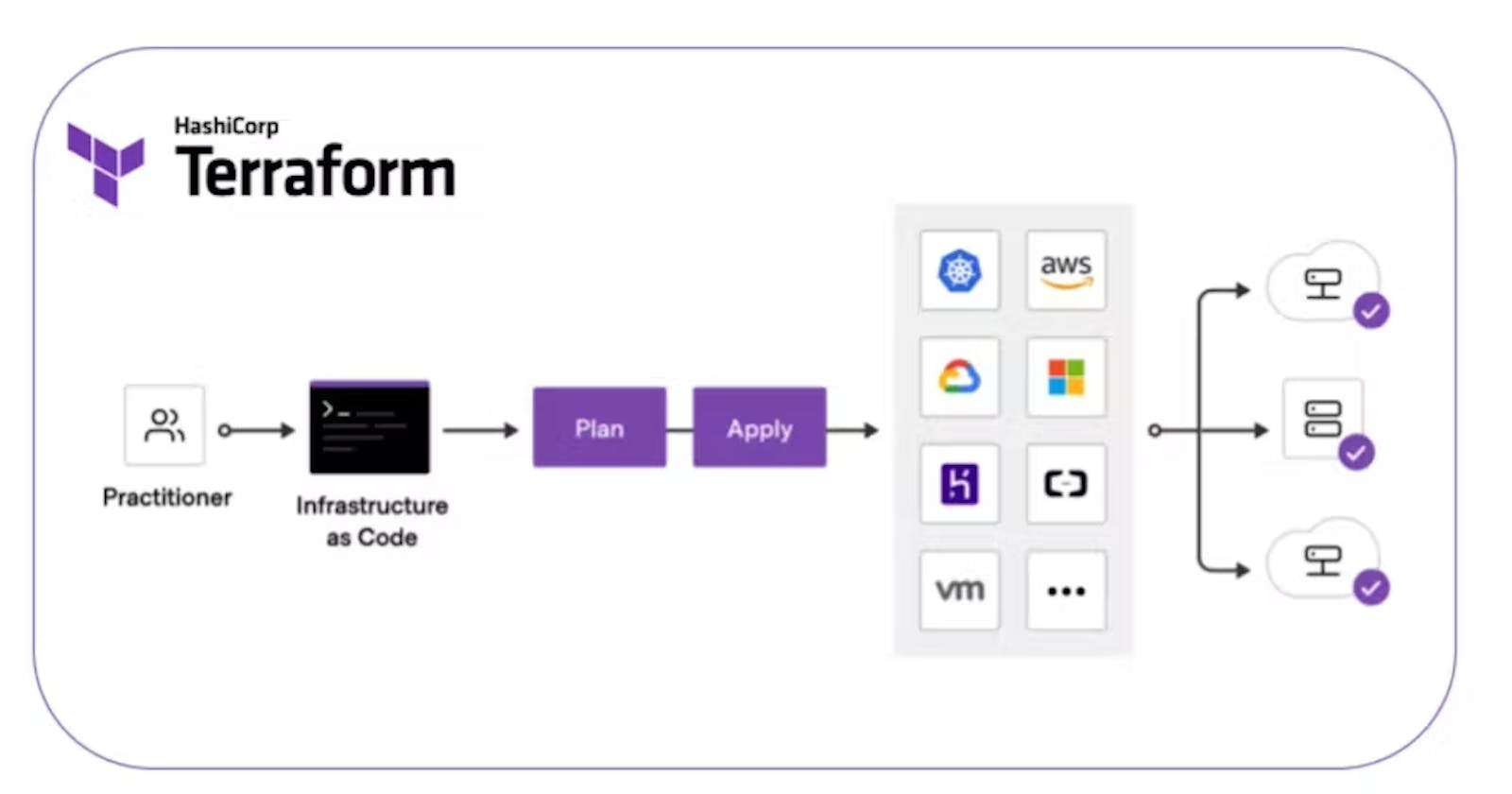
Terraform is a powerful tool that allows you to manage and automate the creation, modification, and destruction of your infrastructure. It works by describing your infrastructure as code, which can be version controlled and easily shared with others.
The basic workflow of Terraform is as follows:
INIT: This is the first step of the Terraform workflow, where you initialize your Terraform environment. This step sets up the necessary files and directories for Terraform to manage your infrastructure.
PLAN: The next step is to create a plan of what changes will be made to your infrastructure. This step allows you to preview the changes that Terraform will make to your infrastructure before actually applying them.
APPLY: The final step is to apply the changes to your infrastructure. This step takes the changes from the plan and makes them live in your infrastructure.
Terraform can be used to manage a variety of different types of infrastructure, including cloud providers, Kubernetes clusters, version codes, DNS providers, and DP (data processing) systems. It is a more advanced tool than others like CloudFormation because it is updated regularly, is not limited to a single cloud provider, and has advanced logic capabilities like conditional Terraform blocks.
To ensure that your Terraform code is of high quality and maintainable, it is important to follow certain best practices. These include version controlling your code, using Terraform modules, having a standardized procedure for configuration, using workspaces for different environments, and having consistent naming conventions.
Another important aspect of Terraform is the use of outputs and imports. Outputs allow you to export data from one Terraform project to be used by another. This creates a layer effect and allows for more efficient management of dependencies. Imports allow you to reference outputs from other Terraform projects, even if they were not created by Terraform. This allows you to use a load balancer from Cloudflare in your AWS infrastructure, for example.
Some useful resources down below:
https://www.reddit.com/r/Terraform/comments/my5b3t/terraform_best_practices/
https://github.com/ozbillwang/terraform-best-practices
You can use Terraform to manage:
- Cloud Providers
- Kubernetes
- Version Codes
- Versioning Codes via version tagging in Git
- DNS Providers
- DP ( Used by many companies worldwide, and some of them open-sourced their entire codebase )
Terraform are:
- More advantageous since it is updated regularly.
- Universal not only used in AWS. (e.g. Cloudformation).
- Terraform advanced logic. (Conditional TF blocks.)
The elements of a good Terraform code are:
- Must be version controlled.
- Terraform Modules.
- Standardized procedure for configuration. (e.g. conventions)
- Use workspaces for different environments if the environments are equal. If NOT then use separate projects.
- Naming conventions.
Outputs and Import
- Each project can provide output for its infrastructure to be used by succeeding infra where it will be built on. Creating a layer effect.
- Data that is outputted must be explicitly outputted by the parent layer.
- Terraform outputs from other projects can be referenced to a single project. (e.g. using a loadbalancer from cloudflare instead from AWS) to be used by your infrastructure.
- Dependencies are managed by Terraform.
TFSTATE
- Upload tfstate into remote object storage. (Shared remote storage)
- Do not manipulate tfstate manually, use TF.
- Implement tfstate locking. To protect from concurrent edits. (Not all storage backend supports it).
- Backup statefile (e.g. turn on the versioning) or on a secure location.
- Never save TF state files in git, they can contain sensitive information in plain text format;
MODULES
- Manage modules versions with tags, this will make upgrades and maintanance easier.
LAYERS
- Think of terraform as layers and dependencies. Since you can reference the existing layer using import.
-
ENVIRONMENTS
- 1 state file per environment. (e.g. 1 tf state for production and 1 tf state in development, separation.)
- Terraform Layers https://www.padok.fr/en/blog/terraform-iac-multi-layering
- Run Terraform from a pipeline job for auditability.
- Unit test into Terraform (e.g. ConfTest)
- Everytime you run Terraform update it as you run with it to avoid future problems.
- Create different environments: dev, test and prod.
- best directory structure
- modules, dont reinvent the wheel, just make some improvements.
Useful Implementations:
- Terragrunt
- env0
- Infracost
https://www.reddit.com/r/Terraform/comments/my5b3t/terraform_best_practices/
reddit.com/r/devops/comments/s026wc/does_an..
github.com/cloudposse/terraform-null-label
github.com/ozbillwang/terraform-best-practi..
terraform.io/cloud-docs/guides/recommended-..
terraform-best-practices.com
POLICY
- you can run Forseti policies, Hashicorp policies, or Google terraform validator , or Server Spec for pre-apply and post-apply checks.
Documentation ReadMe
1. End State
2. Code
3. Discussion
Resources to keep you updated:
- Terraform blogs, reddit, dev.to
- Best practices in (AWS, Azure, DO, Linode, GCP)
- Book Terraform up and running
- CF PPT