Giving a team member access to a Kubernetes Cluster

Goal for this Article:
- Create an RBAC for a team member that have access to a specific namespace.
OPENSSL: Creating Key, CSR, Certificate Signing Request, Using CA.key and CA.crt to create a CRT for the user
Create a key and a CSR from the created key.
The subj parameters are:
CN=username > sets the common name in the CSR
O=group > sets the organization name in the CSR (thesis-group)
openssl genrsa -out jari.key
openssl req -new -key jari.key -out jari.csr -subj "/CN=jari"
openssl req -new -key jari.key -out jari.csr -subj "/CN=jari/O=thesis-group"
openssl req -noout -text -in jari.csr
openssl rsa --noout --text --in jari.key
Create a CSR component in Kubernetes. kind: CertificateSigningRequest
apiVersion: certificates.k8s.io/v1beta1 kind: CertificateSigningRequest metadata: name: user-jari-csr spec: groups: - system:authenticated request: $(cat jari.csr | base64 | tr -d '\n') usages: - digital signature - key encipherment - client authkubectl create -f csr-jari.yaml
2.1 Or if the above is not working (as I tested it out), then we sign it via the CA and the Key of our K8s cluster
javascriptCopy codeopenssl x509 -req -in jari.csr -CA ~/.minikube/ca.crt -
CAkey \
~/.minikube/ca.key -CAcreateserial -out johndoe.crt -days 364
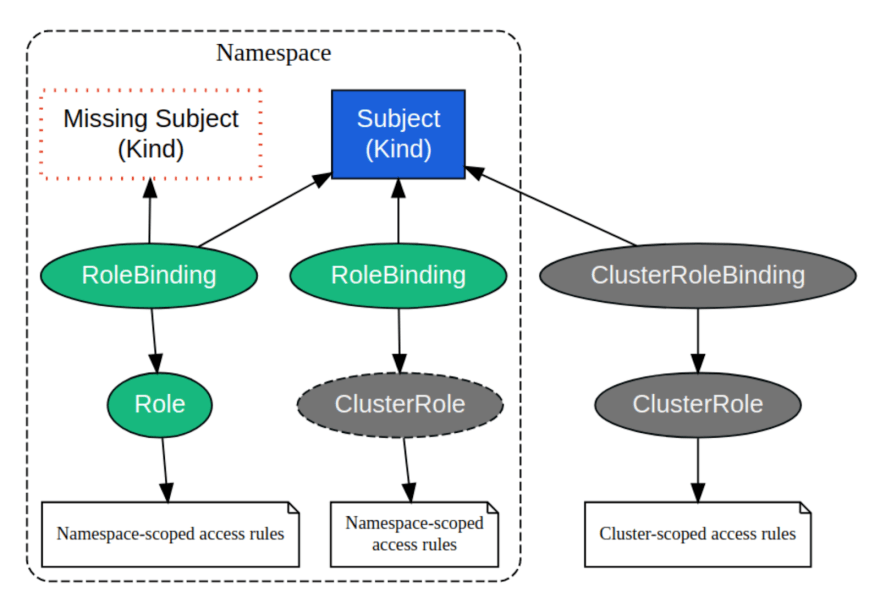
Create a NS and RBAC rules (roles and rolebinding and verb ):
kubectl create namespace jari-workspace kubectl create rolebinding user-jari\ --clusterrole=cluster-admin --user=jari--namespace=jari-workspaceTest the context
APISERVER=$(kubectl config view --minify | grep server | cut -f 2- -d ":" | tr -d " ") echo $APISERVER kubectl config set-cluster jari-cluster \ --insecure-skip-tls-verify=true \ --server='https://127.0.0.1:41457' \ --kubeconfig=jari.kubeconfig * why even when it says that the cluster is created it is not showing in the kube config file ** the reason is that the kubeconfig default is located in /.kube/config and it is not related to our new one. *** use these commands for troubleshooting: kubectl config view --kubeconfig=jari.kubeconfig kubectl config get-contexts --kubeconfig=jari.kubeconfig kubectl config use-context jari --kubeconfig=jari.kubeconfig kubectl config current-context --kubeconfig=jari.kubeconfig *** now we understand the issue, the context is empty when doing the second command because the field --kubeconfig=has no value (before is bob.kubeconfig) **** also, another culprit is if we don't specify the kube config file it will point to the default location, rather we can do this: k get nodes --kubeconfig=jari.kubeconfig kg pods -n jari-workspace --kubeconfig=jari.kubeconfig No resources found in the jari-workspace namespace. kubectl config set-credentials jari \ --client-certificate=jari.crt \ --client-key=jari.key \ --embed-certs=true \ --kubeconfig=jari.kubeconfig kubectl config set-context jari \ --cluster=jari-cluster \ --user=jari\ --namespace=jari-workspace \ --kubeconfig=jari.kubeconfiguse the context:
kubectl config use-context jariWhen encountered with the error:
arduinoCopy codeE0722 21:07:19.592299 80664 memcache.go:265] couldn't get current server API group list: Get "http://localhost:8080/api?timeout=32s": dial tcp 127.0.0.1:8080: connect: connection refused E0722 21:07:19.592891 80664 memcache.go:265] couldn't get current server API group list: Get "http://localhost:8080/api?timeout=32s": dial tcp 127.0.0.1:8080: connect: connection refused E0722 21:07:19.595084 80664 memcache.go:265] couldn't get current server API group list: Get "http://localhost:8080/api?timeout=32s": dial tcp 127.0.0.1:8080: connect: connection refused E0722 21:07:19.598084 80664 memcache.go:265] couldn't get current server API group list: Get "http://localhost:8080/api?timeout=32s": dial tcp 127.0.0.1:8080: connect: connection refused E0722 21:07:19.598646 80664 memcache.go:265] couldn't get current server API group list: Get "http://localhost:8080/api?timeout=32s": dial tcp 127.0.0.1:8080: connect: connection refusedmake sure the server is correct by running
kubectl cluster-infoand use --kubeconfig flag to pass the custom kubeconfigRunning on port 41457... sher@asher-virtual-machine:~/CKA-Extended1$ curl https://127.0.0.1:41457/api curl: (60) SSL certificate problem: unable to get local issuer certificate More details here: https://curl.se/docs/sslcerts.html curl failed to verify the legitimacy of the server and therefore could not establish a secure connection to it. To learn more about this situation and how to fix it, please visit the web page mentioned above. asher@asher-virtual-machine:~/CKA-Extended1$ kubectl cluster-info Kubernetes control plane is running at https://127.0.0.1:41457 CoreDNS is running at https://127.0.0.1:41457/api/v1/namespaces/kube-system/services/kube-dns:dns/proxy To further debug and diagnose cluster problems, use 'kubectl cluster-info dump'.